Inequality & Privacy
Modern financial systems encode structural inequality through asymmetric information access and privacy controls. While regulators demand comprehensive surveillance to combat illicit finance, the infrastructure of compliance systematically disadvantages individuals and smaller market participants who cannot afford sophisticated privacy-preservation technology. This creates a financial system stratified not just by capital, but by access to opacity—where sophisticated market participants exploit regulatory arbitrage while retail investors remain maximally visible.
The tension is not accidental but architectural. Central bank digital currencies, derivatives markets, and anti-money laundering frameworks were designed in eras that assumed financial surveillance was both costless and unambiguously beneficial. Yet each mechanism simultaneously creates new forms of rent extraction and informational advantage. The hedging instruments meant to protect market participants from risk become tools for wealth transfer. Privacy-preserving technologies emerge not to protect individuals, but to allow regulators to surveil more comprehensively.
This research program investigates the political economy of financial surveillance: how privacy concerns map onto inequality structures, how regulatory architecture reproduces advantage, and how the technical mechanisms of modern finance encode power relationships that transcend traditional notions of market efficiency.
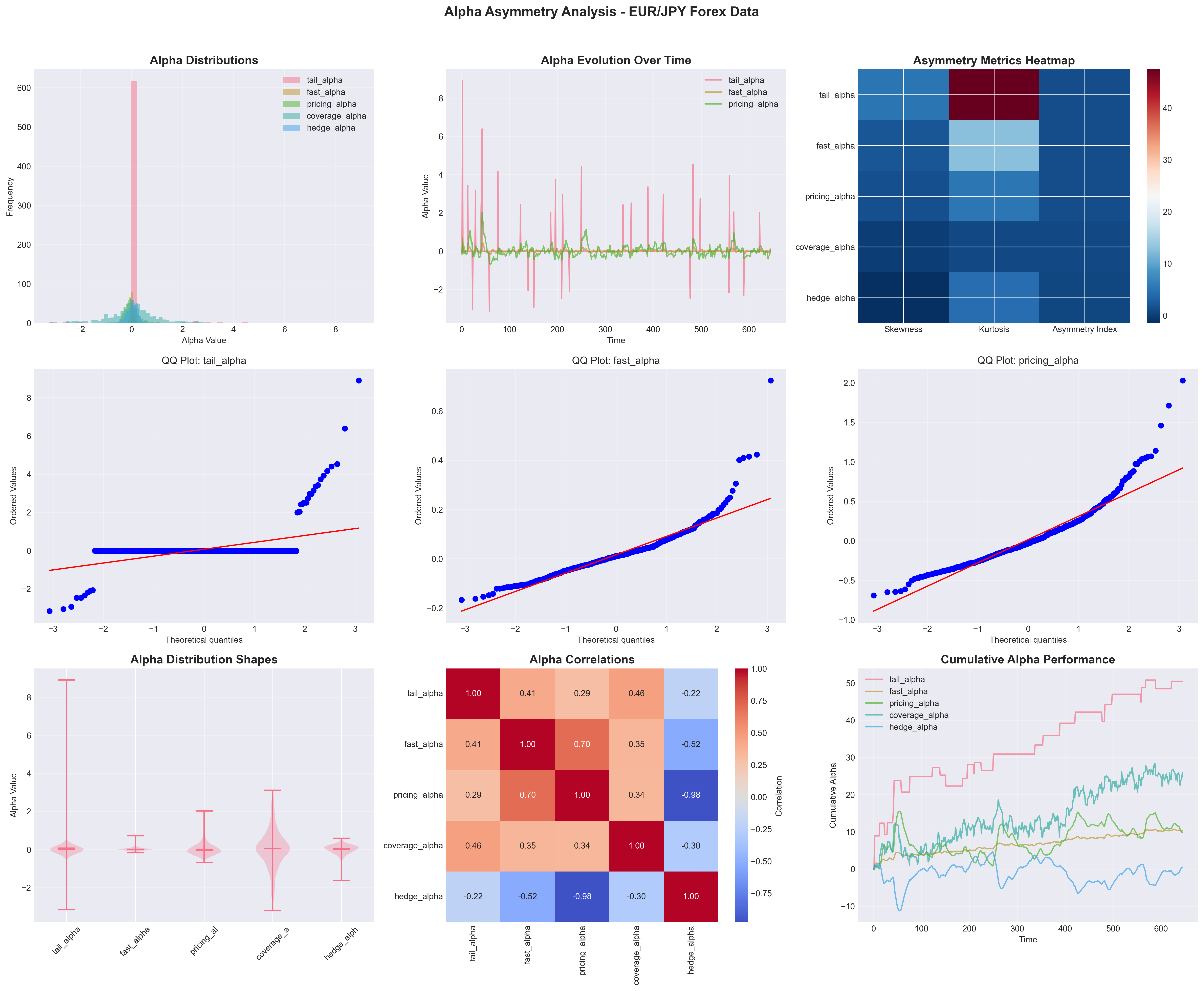
Return distribution asymmetries in major currency pairs: structural advantages manifest as persistent skewness patterns inaccessible to retail participants.
Research Questions
- Privacy Asymmetries: How do privacy asymmetries in financial systems reproduce and amplify wealth inequality? If privacy-preservation technology is expensive, who gains protection and who remains surveilled?
- Hidden Costs of Surveillance: How do compliance frameworks extract rents from those seeking protection while enabling evasion for those with sufficient sophistication?
- Privacy-Preserving Compliance: Can regulatory objectives (AML/CFT) be achieved without exposing transaction-level behavior? What are the technical and institutional barriers?
- Hedging as Wealth Transfer: How do derivatives markets simultaneously function as risk protection and wealth transfer mechanisms? What structural properties enable this?
- Protection vs. Transfer: Where is the boundary between legitimate financial protection and illicit wealth transfer? How do regulatory frameworks fail to distinguish these?
Papers in This Program
Privacy-Preserving Financial Surveillance: CBDC Architecture
Central bank digital currencies represent an inflection point: they can be designed to maximize either surveillance or privacy. Proposes an architectural framework using zero-knowledge proofs and secure multiparty computation to enable regulatory compliance without exposing individual transaction patterns. Demonstrates that privacy and regulatory effectiveness need not be zero-sum.
Alpha Asymmetry in Foreign Exchange Markets
Documents empirical evidence of skewness and kurtosis anomalies in major currency pairs that persist across time periods and market regimes. The asymmetry represents either unexploited profit opportunities or evidence of systematic market failures that privilege certain traders over others. Essential for identifying where market structure itself creates inequality in access to returns.
Asymptotic Protection: Remedy and Poison of Risk Management
Complete hedging is theoretically impossible under incomplete markets, yet partial hedging remains economically essential. This creates a structural necessity tax: those seeking protection must pay sophisticated counterparties for partial hedging, extracting systematic wealth transfers. Protection and predation become indistinguishable.
The Hedging Paradox
AML regulation attempts to distinguish between legitimate financial transfers and illicit wealth movement, yet the mechanisms are structurally similar. Fourth-stage AML frameworks expose ordinary economic behavior while sophisticated actors exploit regulatory complexity. The boundary between protection and transfer is not a line but a spectrum.
Methodological Approach
Computational Analysis
Quantitative investigation of market microstructure asymmetries using skewness/kurtosis estimation and cross-sectional comparisons.
Cryptographic Design
Technical specification of privacy-preserving protocols using zero-knowledge proofs and secure multiparty computation.
Regulatory Analysis
Formal examination of AML/CFT framework efficacy through institutional analysis and game-theoretic modeling.
Market Microstructure
Theoretical investigation of incomplete markets, hedging necessity, and rent extraction mechanisms in derivatives pricing.
Throughline
These papers share a unifying insight: financial inequality is not an accident or market failure to be corrected, but an architectural feature encoded into surveillance systems, regulatory frameworks, and market microstructure. Privacy Asymmetry emerges because sophisticated actors can afford opacity. Market Asymmetry appears in return distributions reflecting structural advantages. Hedging Asymmetry creates wealth transfer because incomplete markets force those seeking safety to pay rents. Regulatory Asymmetry permits sophisticated evasion while exposing ordinary behavior.
The common thread: systems designed to reduce or manage inequality often reproduce it through the very mechanisms intended to address it. Understanding this requires treating inequality not as amenable to technical correction, but as a design feature requiring explicit architectural choice.
Explore the Archive
Access all working papers and preprints in this collection.